
Across enterprise, healthcare, and government sectors, Apple devices have become a staple in the modern workplace.
As their adoption grows, so does the need to maintain a strong security and compliance posture. Organizations must ensure their macOS and iOS deployments align with an expanding set of regulatory and industry standards (CIS Benchmarks, HIPAA, SOC 2, and NIST, to name a few) to protect sensitive data and meet audit requirements.
However, achieving compliance isn't simply a matter of enabling the right settings once.
While initially configuring a device securely is necessary, the greater challenge lies in maintaining continuous compliance as standards evolve, operating systems update, and the threat landscape changes.
This compliance gap, between initial setup and ongoing assurance, creates significant uncertainty. As a result, many fast-moving and heavily regulated industries struggle to maintain compliance across their device fleets.
The Jamf Compliance Editor addresses this challenge directly. Designed specifically for security and IT teams managing Apple fleets, it streamlines the configuration process.
This article explores the challenges of maintaining Apple device compliance, examines where traditional approaches fall short, and demonstrates how tools like the Jamf Compliance Editor help organizations establish a strong baseline for secure, framework-aligned deployments.
Before diving into what the Jamf Compliance Editor offers, it’s important to understand why compliance is a critical concern for organizations (any company, regardless of size or industry).
For organizations managing Apple devices in regulated environments, broader adoption comes with increased scrutiny and a need for comprehensive security controls. Compliance isn’t optional, and it’s essential for maintaining customer trust, avoiding costly penalties, and protecting sensitive data from breaches.
Despite Apple’s strong security foundation, default system settings frequently don’t meet enterprise or regulatory benchmarks. Without proper hardening and ongoing monitoring, devices can expose organizations (any company, regardless of size or industry) to significant risks that may lead to devastating consequences.
Whether mandated by governmental regulation or required by customers and partners, compliance is a critical business necessity. Organizations must demonstrate adherence to widely recognized frameworks such as:
These frameworks are purpose-built, serving as resources for organizations to build their compliance programs and helping reduce the risk of breaches, data loss, and operational downtime by enforcing standardized security configurations across systems and endpoints.
Failing to uphold compliance standards and regulations can have serious consequences ranging from:
Compliance extends beyond just avoiding penalties. It’s fundamentally about protecting organizational data, safeguarding customers, and preserving brand credibility.
The key to effective compliance lies in proper tooling, our next focus.
The Jamf Compliance Editor is an open-source tool that enables IT and security teams to configure Apple devices according to recognized security benchmarks.
Developed by Jamf, this tool streamlines the implementation of industry-standard security controls across macOS, iOS, iPadOS, and visionOS platforms. Specifically designed for generating CIS-aligned configuration profiles, the Compliance Editor helps enforce secure settings across device fleets.
While Jamf Compliance Editor is free and open-source, it works seamlessly with Jamf Pro, the company's enterprise-grade device management platform. Through this integration, Jamf Pro delivers comprehensive tools for deploying, configuring, and managing Apple devices at scale, while also connecting with Jamf Protect for enhanced macOS security and Jamf Connect for streamlined identity authentication.
💡Note: Jamf Compliance Editor was originally built to support macOS hardening and auditing. While it now includes baseline support for iOS, iPadOS, and visionOS, some features (such as shell script generation and Jamf Pro Extension Attributes) remain exclusive to macOS. Jamf software supports a wide range of Apple devices, including Mac, iPhone, and iPad, and can scale to meet the unique needs of organizations across industries.
The Jamf Compliance Editor streamlines device configuration by providing:
Additionally, Jamf offers comprehensive features including:
The implementation process is straightforward: security teams create configuration profiles, which help organizations manage device settings efficiently, and are then deployed through a Mobile Device Management (MDM) solution.
For the configuration profiles, organizations have the ability to choose from supported CIS Benchmark versions to define a security baseline. From here, you can review and customize the benchmark, enabling or disabling specific controls based on your organization’s security policy.
From here, the Jamf Compliance Editor will provide you with a few outputs:
In summary, the Compliance Editor provides hardened configurations, customization options, and deployment profiles, streamlining the process of securing device configurations. By automating these traditionally manual compliance tasks, it significantly improves the IT team's efficiency. All that is left is to deploy the configuration profiles and scripts to your fleet using Jamf’s MDM, right?
Not quite.
While Jamf Compliance Editor is a powerful tool for establishing a secure baseline, it is important to understand where its responsibilities end.
Jamf Compliance Editor is a powerful starting point, but staying compliant requires more than a one-off deployment. Organizations need additional tooling and monitoring to bridge the gap between deployment and continuous compliance. Additionally, not everything is visible to Jamf; Jamf ensures that the right compliance settings are in-place, but doesn't secure sub-OS level entities. For example, browsers are often used to access sensitive information, and a secured hard drive or installed firewalls don't eliminate the threat of a nefarious Chrome extension. For such an attack vector, a more dedicated tool like Feroot is needed.
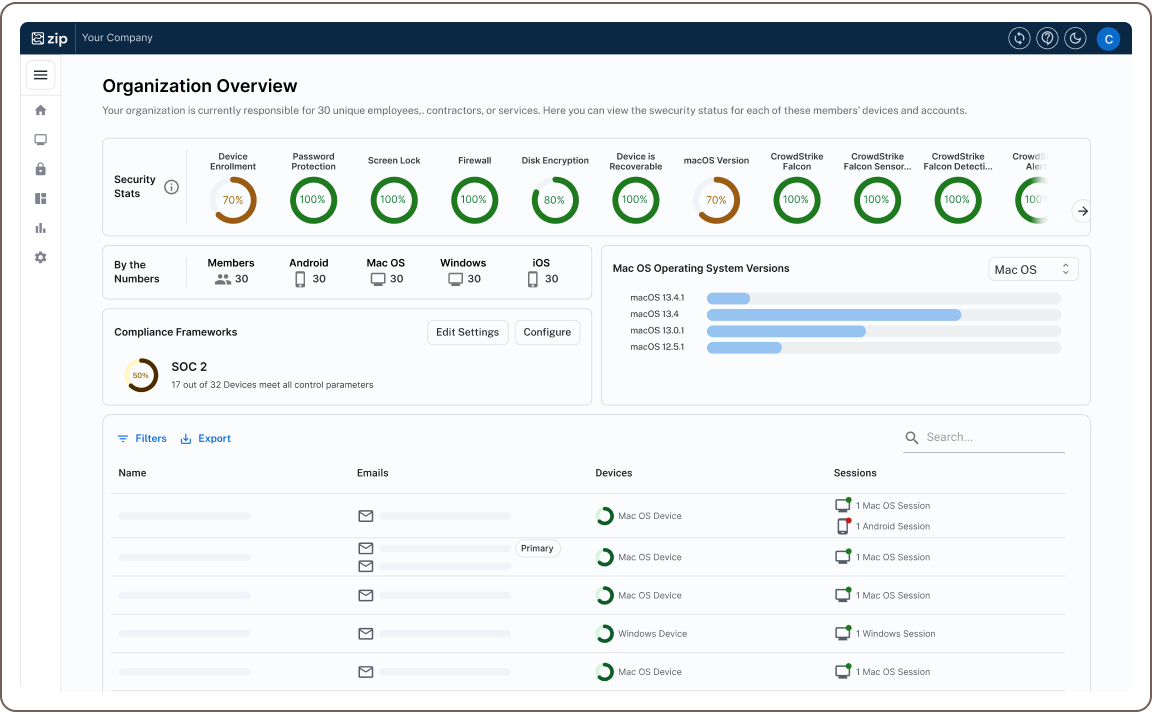
Zip Security extends the capabilities of the Jamf Compliance Editor by providing a comprehensive software solution for protecting organizational resources and ensuring compliance, as well as continuous monitoring of deployed configurations.
While Jamf Compliance Editor establishes the initial baseline, Zip Security transforms these static configurations into a dynamic compliance system that actively monitors your environment in real-time.
The core capabilities of the ZipSec platform include:
In addition to these core capabilities, Zip Security extends beyond Jamf-managed environments by monitoring unmanaged devices and endpoints. This provides organizations with a comprehensive, unified compliance dashboard across heterogeneous device fleets, regardless of the MDM solutions in use.
Cool, now we understand the workflow. The Jamf Compliance Editor creates the configuration, Jamf Pro handles deployment, and Zip Security provides ongoing monitoring. Let's explore some practical applications:
This powerful integration offers numerous additional applications beyond what we've outlined. As regulations evolve and new operating system versions are released, organizations can rely on the combined strengths of Jamf Compliance Editor and Zip Security to adapt quickly.
The Jamf Compliance Editor serves as a crucial foundation for establishing secure device configurations in your Apple fleet.
However, maintaining compliance requires ongoing vigilance and monitoring. By combining Jamf Compliance Editor with Zip Security's continuous monitoring capabilities, organizations can effectively maintain their security posture, demonstrate compliance to stakeholders, and respond swiftly to emerging threats. Zip Security helps teams stay secure, prove it, and act fast.
Ready to strengthen your Apple device compliance? Book a demo to see how Zip Security can transform your compliance workflow.