Most teams don’t fail audits because they misunderstand security; they fall behind because security never stands still.
Controls that pass an audit gradually drift as teams add devices, onboard users, and update tools. Evidence that once held up in audit trails becomes outdated—ownership blurs. When the next audit or customer questionnaire arrives, teams scramble to rebuild proof under pressure—often disrupting everyday work.
This blog dives into why that pattern is so common and how continuous compliance monitoring closes the gap by keeping controls enforced, evidence current, and compliance status clear all year.
Most organizations still treat compliance as a project instead of a system. Here’s how it usually plays out in practice:
On paper, this looks successful. In reality, it creates fragile security and an unstable audit process.
Audits are point-in-time snapshots. They show what was true during a narrow window—not what stays true afterward. Once audit pressure fades, the environment immediately starts changing again:
Over time, ownership becomes unclear. Evidence that passed the audit quickly becomes outdated. What passed once is no longer guaranteed, leading to hidden compliance issues that surface late.
Compliance drift happens because modern environments change faster than teams can keep up manually, especially when one or two people own IT, security, onboarding, audits, and incident response.
Most security teams already understand the underlying compliance requirements. The real challenge is maintaining compliance six months later with limited time and staffing. That’s why a different operating model is required.
Continuous compliance monitoring is the practice of automatically verifying that security controls remain enforced and that audit evidence stays current as systems change—rather than rebuilding proof manually before each audit.
It’s essential to be clear about what this is not:
Continuous compliance monitoring focuses on what matters operationally. It provides:
Traditional compliance is audit-driven. Continuous compliance is system-driven.

Manual compliance creates workload spikes and operational disruptions. Teams pause everyday work to prepare for audits, then resume once the deadline passes. Gaps often surface only when auditors or customers point them out.
Continuous compliance distributes work over time, keeps controls in place, and surfaces issues early—supporting proactive risk assessment rather than reactive fixes.
To understand why this model works in practice, it helps to look at how continuous compliance monitoring operates as a system.
At its core, continuous compliance monitoring operates as a system. It runs through clear, repeatable steps that keep controls enforced and evidence up to date as environments change.
Teams begin by defining what “good” looks like using frameworks such as SOC 2 or ISO 27001, aligning controls with recognized compliance standards.
This step doesn’t introduce new requirements. It formalizes existing expectations into precise, enforceable controls—such as encryption, patching, access management, and endpoint security—mapped directly to the framework criteria.
Teams enforce controls through the tools they already rely on:
These automated tools handle enforcement. The system ensures consistency over time.
As environments change, the system uses automated monitoring to verify that controls remain active.
If a device falls out of policy or a configuration drifts, the system surfaces the gap immediately—rather than months later during an audit.
The system continuously captures logs, configuration states, and coverage data as evidence, supporting both internal audits and external reviews.
That evidence reflects the real state of the environment—not screenshots gathered under deadline pressure.
The system keeps evidence up to date as controls, systems, and requirements change—including when supporting new enterprise customers with slightly different but compatible audit expectations.
Reporting remains current without rebuilding evidence under audit deadlines.
Even teams with strong tools run into operational friction.
Common issues include:
The problem isn’t tool quality. It’s the lack of coordination, visibility, and ongoing enforcement over time.
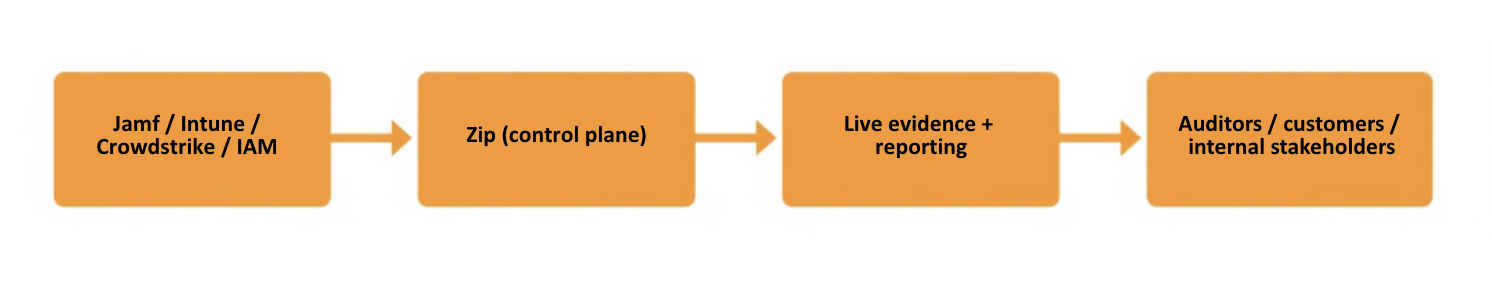
That’s where Zip comes in. Zip doesn’t replace Jamf, Intune, or CrowdStrike. It sits above them as a system layer that unifies visibility, enforcement, and evidence across the environment.
Zip acts as the security and IT control plane that makes continuous compliance practical to run.
Zip gives teams one place to see device posture and access state across their environment, bringing device management and identity context together in a single view. You can quickly tell what’s enrolled, what’s protected, and what’s drifting—without jumping between Jamf, Intune, and identity tools.
This shared view helps teams spot gaps early, before audits or customers surface them.
Zip keeps security baselines enforced after deployment. As devices, users, and policies change, Zip ensures required controls remain in place rather than quietly degrading over time.
That means fewer surprises—and far less manual checking.
Zip collects evidence directly from the real system state. Logs, configurations, and coverage data stay up to date without relying on screenshots or last-minute exports.
Teams don’t have to remember to “capture proof.” The system does it continuously.
Zip keeps reporting continuously as audit-ready for both new and existing clients. Evidence stays current as requirements evolve, without quarterly rebuilds or deadline-driven scrambles.
Audits become reviews—not fire drills.
Zip doesn’t replace the tools teams already trust. It connects Jamf, Intune, and CrowdStrike so they work as a coordinated system instead of isolated components.
Each tool keeps doing its job. Zip makes sure they stay aligned.
For SOC 2 specifically, continuous compliance changes the experience in practical ways.
Teams see:
For IT teams managing audits with limited staff and constant competing priorities, this model replaces stress with predictability. Instead of rebuilding evidence each cycle, teams walk into audits knowing their controls and proof are already in place.
Not every platform supports continuous compliance in practice. Look for a system that:
If a platform still depends on manual checks or heavy prep work, it isn’t solving the core problem.
Zip exists to close the gap between audit expectations and real-world operations. By acting as a system layer above existing tools, Zip keeps controls enforced, evidence current, and ownership clear—without adding more manual work for already stretched teams. The result is simple: audits stop feeling like emergencies, security becomes easier to explain, and teams regain time to focus on day-to-day operations that support business growth instead of constant prep.
Ready to see continuous compliance in your own environment? Discover how Zip can get you compliant in 14 days—and keep you that way.
No, but it significantly reduces audit risk, effort, and last-minute work.
Zip pulls evidence directly from the live system state instead of relying on manual screenshots or exports.
Yes. Zip operates alongside these tools and keeps them enforced as a system.