
Choosing between Endpoint Detection and Response (EDR) tools and Managed Detection and Response (MDR) services is rarely as simple as vendor marketing makes it sound. Both aim to stop threats before they cause real damage, but they take very different approaches.
EDR gives you the technology to detect and respond to suspicious activity on your endpoints, but it’s up to your team to manage it. MDR layers on human expertise, with a dedicated team monitoring and responding to threats around the clock.
The right path depends on your team’s resources, expertise, and tolerance for risk. In this guide, we’ll break down what each option actually does, when it makes the most sense, and how to decide which approach fits your organization.
Endpoint Detection and Response (EDR) involves spotting and containing attacks at the device level – laptops, servers, workstations, and mobile devices, collectively known as endpoints. Unlike traditional antivirus software which mainly looks for known bad files, EDR tracks how processes behave in real time and flags patterns that suggest malicious activity.
To do this, EDR typically installs a small piece of software called an agent on each endpoint. The agent runs in the background, monitoring activity on that device and sending security data back to a central platform for analysis.
Because every operating system works differently, EDR agents integrate at different layers:
All this telemetry is sent to a central platform that’s usually cloud-based where machine learning models and behavioral analytics try to separate normal activity from potential threats. When something looks suspicious, the EDR will automatically respond by isolating the device, stopping processes, quarantining files, and collecting forensic data for investigation.
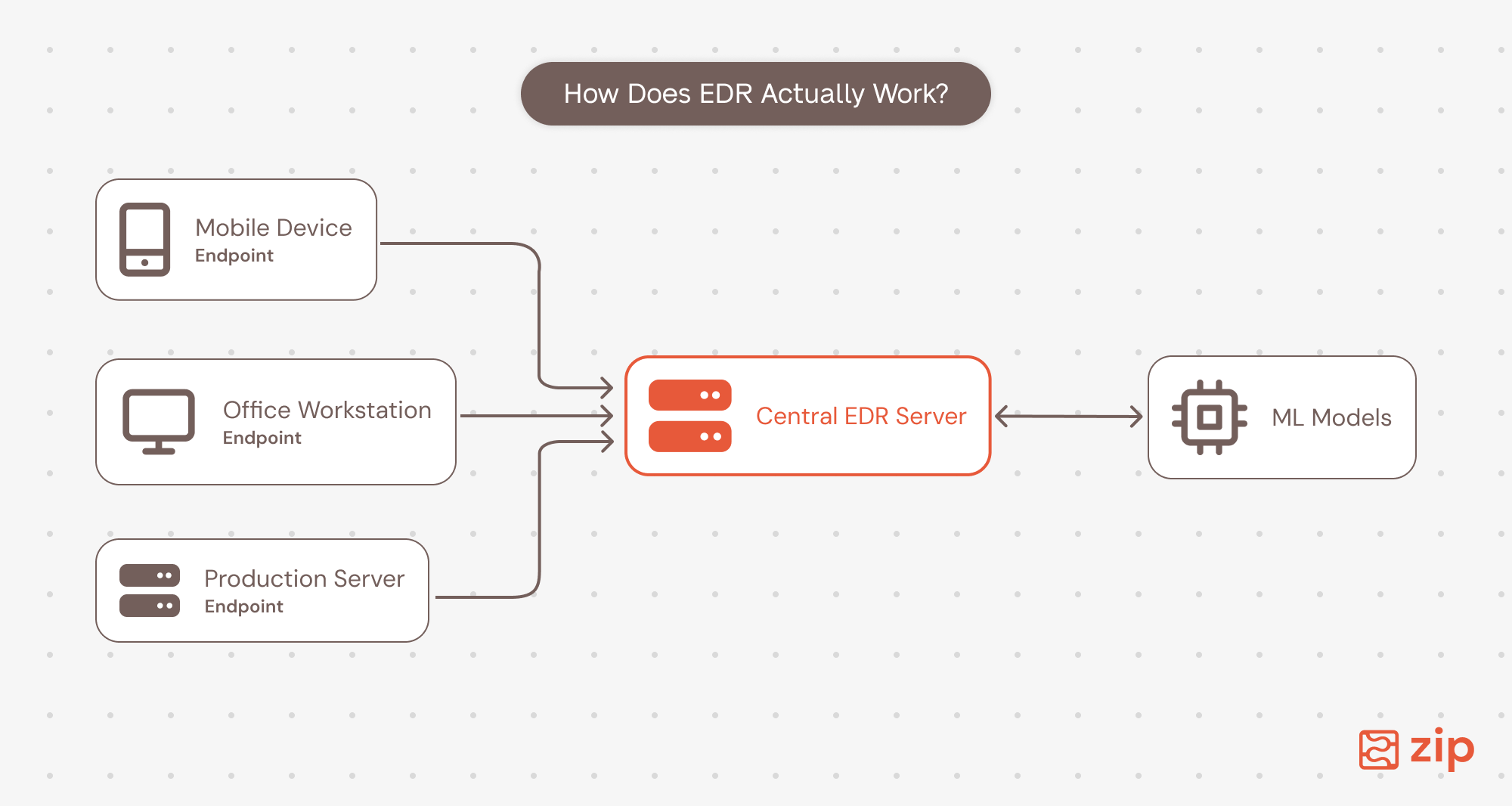
The key difference from traditional security tools is that EDR assumes a breach will happen. Instead of just trying to prevent attacks, it focuses on detecting them quickly and containing the damage. It's designed for the "when, not if" mindset that most security teams have adopted.
Leading providers in this space include CrowdStrike and SentinelOne, among others.
The key difference between Endpoint Detection and Response (EDR) and Managed Detection and Response (MDR) is who is in charge of monitoring and managing alerts. Whereas EDR software is typically managed by the organization that buys it (or an external resource like an MSP), MDR offerings let you outsource threat detection and response to a team of security professionals who monitor your environment 24/7/365.
Here's how MDR works in practice: the provider deploys their tools across your environment (often including EDR agents, network sensors, log collectors, and cloud monitoring). From there, a team of security operations center (SOC) analysts monitor everything 24/7. When they spot something suspicious, they don't just send you an alert: they investigate it, confirm whether it's a real threat, and take immediate containment actions.
The "managed" part is crucial. If ransomware starts encrypting files on a server at 3 AM, the MDR team is already investigating and isolating the affected systems before your on-call engineer even gets paged. They're not just monitoring; they're actively responding.
Some MDR services also include threat hunting. This entails proactively searching through your environment for signs of advanced persistent threats that might have slipped past automated detection. They'll dig through weeks or months of historical data looking for subtle indicators that something isn't right.
The scope often extends beyond just endpoints too. Many MDR providers monitor network traffic, cloud service logs, and identity systems to get a complete picture of what's happening across your entire infrastructure. This broader visibility can catch attacks that might not be obvious when you're only looking at individual endpoints.
The choice between EDR and MDR comes down to a few key factors that go beyond the technology.

EDR requires you to have security analysts who can investigate alerts, tune detection rules, and respond to incidents. If you get 50 alerts during a widespread attack, your team needs to triage all of them and figure out which ones are real threats.
MDR providers handle that triage for you and only escalate confirmed threats.
EDR gives you deep visibility into individual endpoints, but that's where it stops.
MDR typically provides broader coverage across your entire environment, looking at data sources including endpoints, network telemetry, cloud logs, and identity systems. The MDR analysts can correlate events across all data sources to spot attacks that might not be obvious from any single system.
With EDR, you have complete control over detection policies, response procedures, and how the system integrates with your existing tools. You can customize everything to fit your specific environment and requirements.
MDR trades some of that control for convenience: providers typically use standardized procedures, and you have less ability to customize their response playbooks. That said, some MDRs will use your existing EDR solution, but this may impact pricing.
EDR licensing is typically priced per endpoint or user. It does not include deployment, configuration, or ongoing management, costs that ultimately fall on your company.
MDR is full service with higher pricing due to the included human expertise: MDR staffers are highly trained on how to handle alerts. The upside is that you need fewer internal security staff while simultaneously getting more complete coverage.
MDR shines at response speed. When an attack happens outside business hours, an MDR team is already investigating before your internal team even knows there's a problem yet.
For organizations without 24/7 security coverage, this can be the difference between containing an incident and dealing with a full breach.
In-House Expertise
Your company has a mature security operations team that can handle alert investigation and incident response. You’re able to deploy EDR across all your endpoints and keep agent patches up-to-date. Your team has the capacity to respond to incident alerts and contain them as they emerge.
Highly Sensitive Data
You're dealing with highly sensitive environments where you can't allow external access. You simply can't have third-party providers accessing your systems, even for security monitoring.
Higher Risk Tolerance
You're dealing with highly sensitive environments where you can't allow external access. You simply can't have third-party providers accessing your systems, even for security monitoring.
Personalization
You want the granular control to tune detection rules for your specific environment and integrate the EDR data with your existing security tools.
No In-House Expertise
You don’t have the internal manpower or expertise to monitor and respond to alerts around the clock, taking follow-up action where necessary. Threat actors sometimes target times they know there will be fewer people monitoring, with Cyberhaven suffering a Christmas Eve attack earlier this year.
Noisy Signals
If you have a busy product, you’ll easily become overwhelmed by alert fatigue. If your current security tools are generating hundreds of alerts per day and your team is struggling to keep up, MDR can help filter out the noise and only escalate real threats.
Time-To-Secure
You need to quickly improve your security posture. After a security incident or to meet new compliance requirements, MDR can provide immediate expert-level monitoring while you build up internal capabilities.
Limited Engineering Bandwidth
If you have limited engineering bandwidth, you’ll want broader coverage without the complexity. Instead of deploying and managing separate tools for endpoint, network, and cloud monitoring, many MDR providers can give you comprehensive coverage through a single service.
For many companies, the right answer isn’t strictly EDR or MDR – it’s a combination of both. A hybrid approach allows organizations to deploy and manage EDR directly, giving them deep visibility and control at the endpoint level, while layering on MDR services for round-the-clock monitoring and expert support. This model works well for teams that have some in-house expertise but want to extend their coverage without building a full 24/7 security operations center (SOC).
At Zip Security, we’ve built our offering around this balance. Our platform automates the deployment, configuration, and ongoing management of CrowdStrike (EDR) in our intermediate package. For teams that need continuous coverage, our advanced package adds MDR capabilities on top of that same CrowdStrike instance – delivering 24/7 monitoring and response at a fraction of the cost of most MDR services.
Pursuing an EDR or MDR strategy is the right approach to building a more robust security posture. However, EDR and MDR are designed for very different teams (with hybrid approaches for teams in the middle).
For teams with seasoned security employees, EDR might be the right choice. It gives you the right tooling for your personnel to spring into action and tackle issues. However, many teams don’t have that 24/7 staffing needed. For those, MDR provides an end-to-end, managed solution that doesn’t compromise on security.
In a summary, ask yourself a few practical questions:
Of course, there are hybrid strategies. For teams that have internal capabilities, but need to improve their security posture immediately, MDR might be the preferred solution until an EDR motion could be carefully planned out and implemented. Or, teams could go with a permanent hybrid, where EDR is implemented to give teams access and visibility to their endpoints, but a MDR team interfaces with the tooling to provide staffing coverage.
At the end of the day, both approaches can lead to a robust security posture. What matters is choosing a strategy that actually fits your team’s needs.