
If you sell to larger customers, you feel the shift. Security reviews move from “nice to have” to a first-stage gate. Vendor questionnaires get longer. Procurement asks for proof, not promises.
Here’s the reframe that makes this manageable: enterprise compliance requirements like SOC 2 and HIPAA aren’t paperwork. They’re how big customers reduce risk when they buy from smaller vendors. Buyers need a repeatable way to evaluate vendors, especially when your product touches consumer data, supports regulated workflows, or impacts security outcomes across multiple business units.
If you’re a CEO, COO, or CFO at a 5–500 person company, this pressure lands on you. You own the outcome, but you don’t have unlimited time or a dedicated security team. You carry responsibility without complete visibility.
The goal isn’t to memorize a framework. The goal is to run security controls that stay enforced as your environment changes—and remain easy to prove—so compliance becomes a growth lever, not a drain on your team.
If your enterprise customers are increasingly adding compliance requirements to your contracts, book a demo with Zip Security. We'll get you audit-ready (and help you stay that way) in just 14 days.
Enterprise buyers include compliance requirements because procurement has one job: reduce risk in a consistent, defensible way. That risk includes operational disruption, reputational damage, financial risks, and the cost of vendor failure. In regulated environments, it also provides exposure tied to legal requirements and compliance regulations.
In practice, compliance requirements act as a trust filter. When an enterprise buys from you, they take on real exposure:
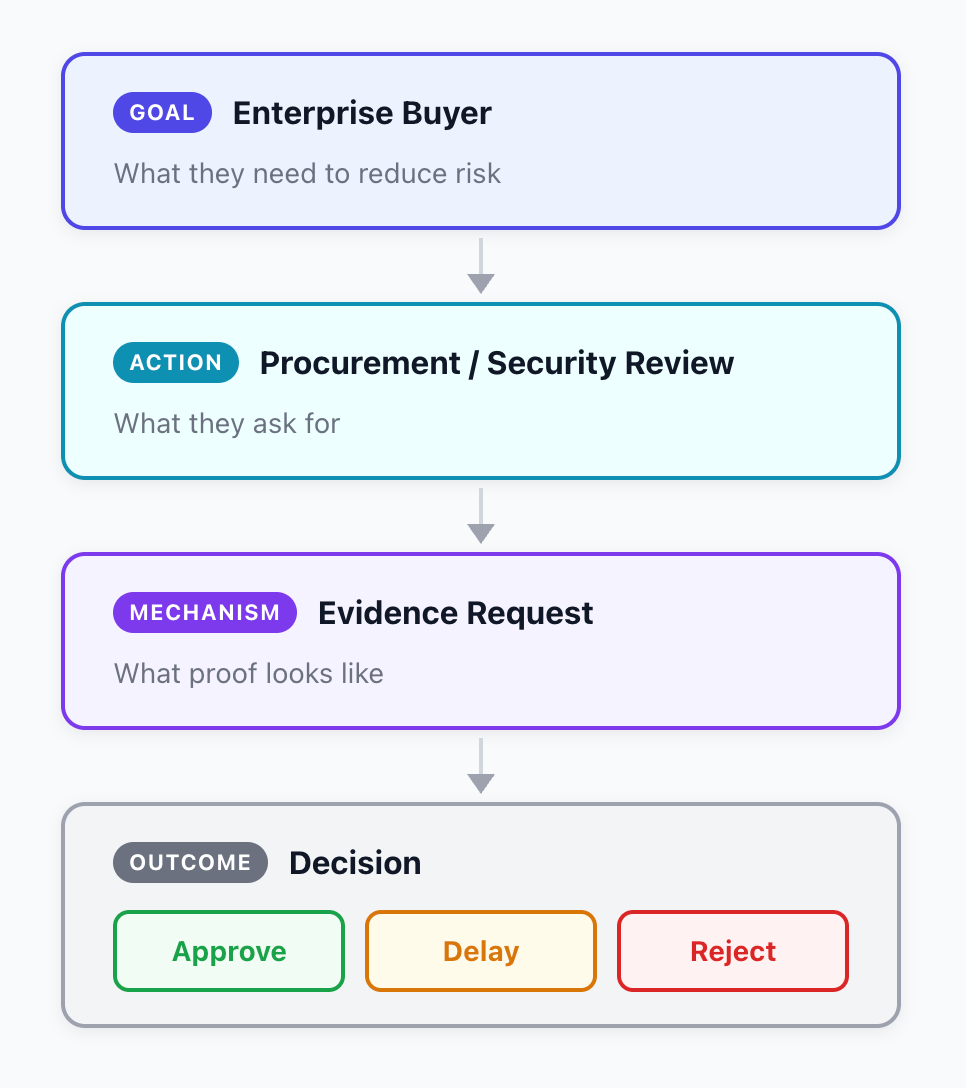
Instead of relying on reassurance, they ask for proof. Procurement can’t personally oversee every vendor across dozens—or hundreds—of partnerships, so they standardize the evaluation process.
Most buyers look for the same three signals, no matter what the checklist says:
Who owns device security, access reviews, endpoint protection, and offboarding? In many organizations, a named compliance officer (or a security owner with compliance responsibility) coordinates internal compliance—but the buyer still wants clarity on who is responsible for what.
A one-time setup doesn’t hold if settings drift as teams, devices, and tools change. Enterprises want controls that behave like systems, not reminders.
Evidence On Demand
Not a last-minute scramble. Not a folder of screenshots. Current evidence that controls exist, stay enforced, and have accountable owners—especially for controls tied to sensitive data, access, and endpoint protection.
That’s why enterprise compliance matters even if you’re not an enterprise company. Buyers expect enterprise outcomes.
SOC 2 and HIPAA can sound like jargon until you view them through a buyer’s lens. Most customers care less about the framework itself and more about what it proves.
SOC 2 signals operational reliability—and sets the foundation for SOC 2 success. It shows buyers that you consistently run security controls over time, including how you manage systems, access, and availability.
HIPAA signals a disciplined approach to handling sensitive data. In healthcare settings, buyers look for privacy and access controls that follow a clear, systematic approach—not ad hoc decisions. They also expect alignment with guidance and expectations from the Health and Human Services (HHS) ecosystem, where HIPAA enforcement and interpretation shape how vendors demonstrate safeguards.
Many buyers also ask about broader compliance regulations depending on where they operate. For example, customers in the EU (or serving EU residents) often care about the General Data Protection Regulation and how you handle personal data, retention, and access.
When a large customer asks about SOC 2 or HIPAA, they’re usually looking for:
That’s the shift: enterprise expectations now apply to SMB and mid-market vendors by default.
Most teams don’t struggle because they don’t understand compliance—they struggle because controls don’t stay true over time.
Modern IT environments change constantly:
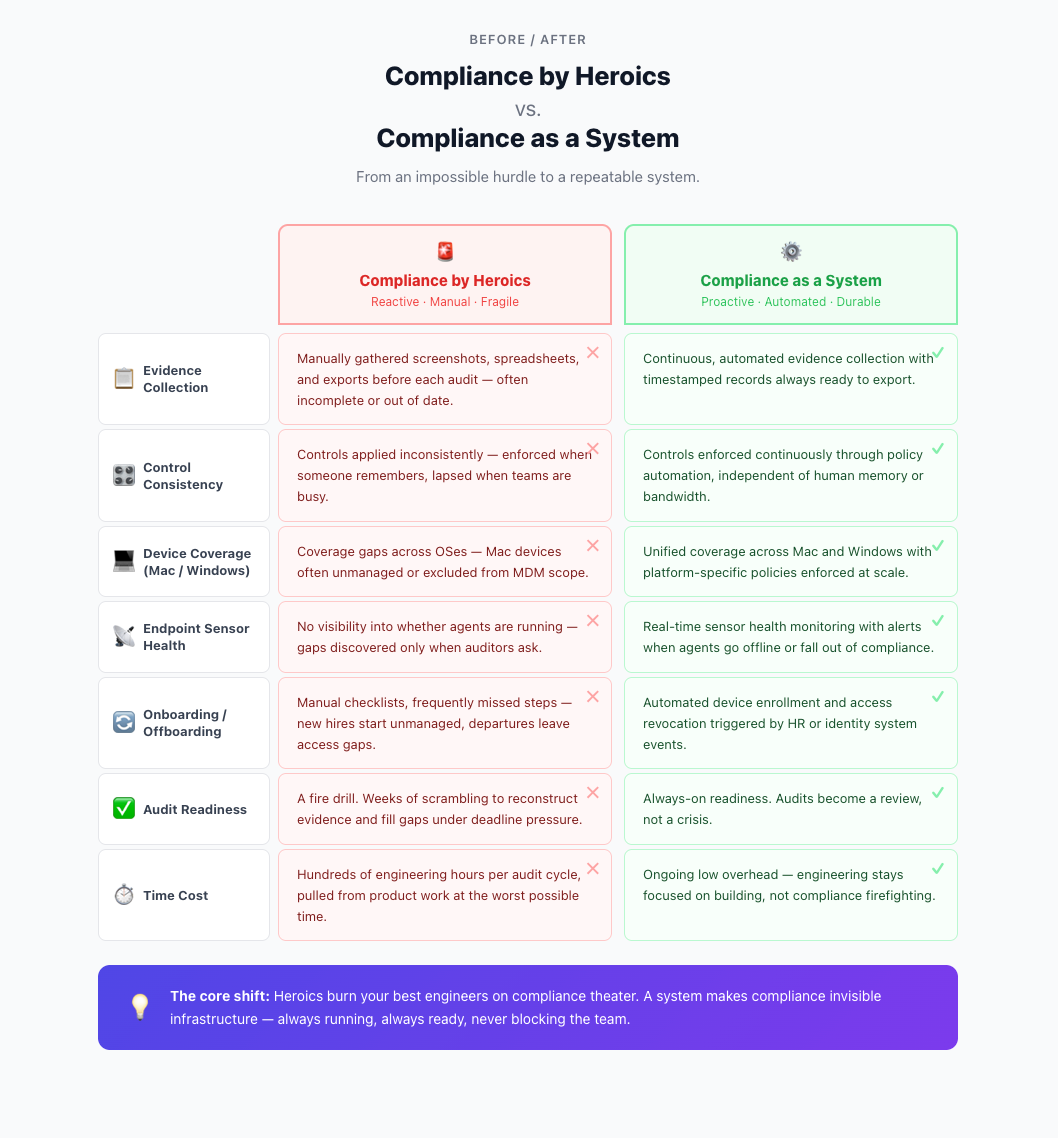
That isn’t a moral failing. It’s normal operations. The failure mode is drift: when controls start out configured correctly but quietly fall out of compliance as the environment changes. Drift also increases the risk of data breaches by widening the gap between what you think is enforced and what actually runs in production.
These are the gaps that most often surface during customer reviews and audits:
A laptop ships but doesn’t enroll correctly. An employee leaves, but access remains longer than it should.
Mac policies live in one place and Windows policies live in another. You end up “mostly consistent” instead of consistently enforced.
You deploy endpoint protection, but sensors fail, devices miss enrollment, or coverage becomes uneven over time.
Permissions accumulate, exceptions become defaults, and reviews happen only when someone asks.
These situations are where Zip’s approach matters: you don’t need more tools. You need controls that stay enforced—and remain easy to prove.
The most practical way to meet compliance requirements is to turn compliance into a simple operating model:
See → Enforce → Prove
This approach aligns with SOC 2, HIPAA, GDPR, and many financial regulations because it focuses on what buyers actually need: coverage, consistency, and evidence. It also supports enterprise compliance risk management by making control performance visible and repeatable.
You can’t prove enterprise security if you can’t see what’s covered. Start with one place to understand:
Outcome: fewer unknowns during security reviews.
Zip acts as a control plane, sitting above tools like Jamf, Intune, CrowdStrike, and Entra ID to give you a single view of what’s enforced, where it’s enforced, and who owns it—without juggling multiple dashboards.
Compliance breaks when enforcement becomes manual. Checklists and periodic spot checks don’t scale for lean teams. The goal is to keep controls aligned as devices and users change—without relying on memory.
Outcome: fewer “we’ll fix it later” gaps and fewer exceptions that quietly become permanent.
Zip supports continuous control enforcement across the tools you already use. It doesn’t replace Jamf or Intune—it helps keep baselines consistent across both. It doesn’t replace CrowdStrike—it helps keep endpoint coverage and sensor health visible and maintained over time.
Enterprise buyers don’t want promises. They want proof. When evidence demands a scramble, compliance becomes a recurring fire drill.
Outcome: faster questionnaires, smoother procurement, and less disruption.
Zip’s compliance and audit readiness approach keeps evidence current, so when a customer asks, you can respond with clarity instead of spinning up a new project.
“Zero extra man-hours” doesn’t mean there’s no work. It means you stop repeating the same work every time a customer asks for proof—because controls stay enforced and evidence stays current.
Why it matters to compliance requirements: Consistent baselines are easier to defend than one-off configurations. Enterprise buyers want confidence that encryption, patching policies, and device settings stay enforced across the entire fleet to protect digital assets.
Zip keeps device baselines consistent across Jamf (macOS) and Intune (Windows), so controls don’t split into two different realities as your company grows.
Why it matters: Enterprise buyers care about coverage and health. “We use an EDR” isn’t the same as “We can show our EDR is deployed and healthy across the fleet”—and that proof is a core part of endpoint compliance.
Zip makes EDR coverage and sensor health visible and auditable over time, narrowing the gap between “deployed” and “working.”
Why it matters: Onboarding and offboarding are where reviews find gaps. When device trust and identity live in separate silos, blind spots appear quickly.
Zip connects device trust and identity context so enrollment, access, and policy gaps surface early—and onboarding and offboarding stay consistent as roles change.
Want to see what “continuous evidence” looks like in a real environment? Book a demo today.
Many teams undersell themselves in security conversations. They either share framework details the buyer didn’t ask for, or they say “we’re compliant” without explaining what that means day to day.
Instead, use calm, specific language that signals control.
These points land because they match what procurement actually needs: consistent enforcement and proof tied to legal requirements, internal policies, and real operational controls.
Compliance requirements shape how enterprise customers buy. You don’t win by memorizing compliance frameworks—you win by running controls that stay enforced as your environment changes and keeping evidence ready without heroics. Zip acts as the security and IT control plane above the tools you already use, so controls stay consistent across devices, identity, and endpoint security—and your posture stays easy to prove when enterprise buyers ask.
Learn more about Zip’s compliance approach—and see how to make compliance provable.
Maintain compliance by treating requirements as ongoing controls and routines, not a one-time project. Keep an accurate inventory of systems and data, enforce baselines across devices and access, monitor for drift, assign clear ownership, and collect evidence continuously so audits and customer reviews don’t trigger a scramble.
Not always. Many enterprise buyers don’t require a specific certification right away—they want confidence and proof that controls are in place and stay enforced. SOC 2 reports or HIPAA-aligned programs can speed trust, but what matters most is showing consistent coverage, clear ownership, and evidence when procurement asks.
Zip keeps controls visible, enforced, and provable across the tools you already use. Instead of relying on manual checks and last-minute screenshots, Zip sits above Jamf, Intune, CrowdStrike, and Entra ID to reduce drift, standardize enforcement, and make evidence easier to produce.